



This article is a sub-topic under Virtualization Technology: Empowering Ethical Hackers And Red Teams For Cybersecurity Excellence
In the realm of cybersecurity, control, and security are paramount concerns. The landscape is constantly evolving, with threat actors devising increasingly sophisticated ways to compromise systems and infiltrate networks. Amidst this dynamic environment, the fusion of virtualization and Command and Control (C2) servers emerges as a critical nexus, offering both enhanced control and strengthened security measures.
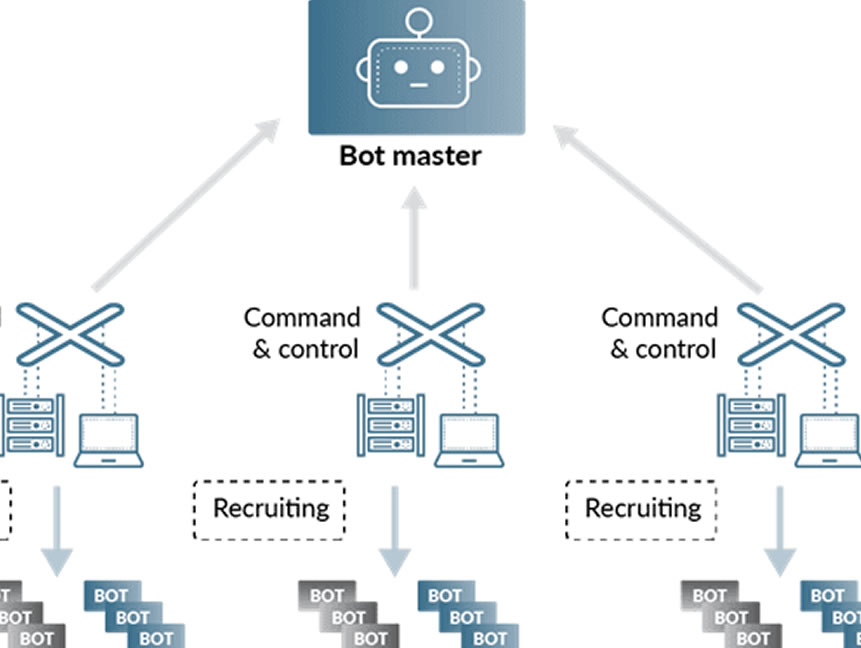
The Essence of Command and Control (C2) Servers:
Command and Control (C2) servers play a central role in cyberattacks, serving as the linchpin for remote communication and coordination between attackers and compromised systems. These servers provide a means for threat actors to manage their malicious operations, deliver payloads, and exfiltrate sensitive data.
For defenders, thwarting C2 communication is a vital objective in preventing and mitigating cyberattacks. This is where virtualization steps onto the stage, introducing a new layer of control and security to the intricate dance between attackers and defenders.
Virtualization’s Role in C2 Security:
Virtualization, with its ability to create isolated and segregated environments, offers a potent tool for enhancing the security of C2 servers. Here’s how virtualization intersects with the realm of C2 security:
Ethical Hacking and Red Teaming with Virtualized C2 Servers:
For ethical hackers and red teams, virtualization offers a controlled and secure platform to simulate real-world attack scenarios involving C2 servers. By creating virtual C2 environments, these professionals can replicate the tactics and techniques of adversaries, assess an organization’s defenses, and identify potential vulnerabilities.
Moreover, virtualization technology empowers red teams to conduct controlled C2 communication exercises, enabling them to evaluate how well an organization detects and responds to such threats. This approach ensures that defenders are well-prepared to thwart actual C2 attacks.
Conclusion: Navigating the Nexus:
The convergence of virtualization and C2 servers presents a compelling synergy in the realm of cybersecurity. As organizations strive to bolster their defenses against cyber threats, virtualization emerges as a strategic ally in enhancing control, security, and preparedness.
By leveraging virtualized C2 environments, organizations can effectively analyze, study, and mitigate potential threats. Ethical hackers and red teams harness this fusion to simulate attacks, test defenses, and strengthen an organization’s resilience against real-world adversaries.
In the complex dance between attackers and defenders, virtualization stands as a partner that empowers organizations to choreograph their moves with precision and purpose. Through this synergy, the nexus of virtualization and C2 servers becomes a potent force in navigating the intricate landscape of control and security in the digital age.
Read More
1. Virtualization and the Ethical Hacker’s Playground: Explain how virtualization creates a secure playground for ethical hackers and red teams to practice their craft. Discuss the benefits of isolating testing environments and utilizing virtual snapshots for quick recovery during intensive hacking exercises.
2. Unleashing the Red Team: Real-World Simulations through Virtualization: Explore how red teams use virtualization to conduct real-world simulations of cyberattacks. Discuss the strategic value of creating diverse virtual scenarios to identify vulnerabilities, assess risks, and enhance an organization’s overall cybersecurity posture.
3. The Role of Virtual Machines in Penetration Testing: Highlight the significance of virtual machines in penetration testing. Discuss how ethical hackers leverage VMs to perform penetration tests on various operating systems and applications while keeping the production environment safe from unintended consequences.
4. Building an Agile and Scalable Hacking Infrastructure: Guide ethical hackers and red teams on building an agile and scalable hacking infrastructure using virtualization. Discuss the benefits of cloud-based virtualization and orchestration tools in managing larger-scale engagements and assessing complex network topologies.
5. Virtualization and C2 Servers: Navigating the Nexus of Control and Security: Amidst this dynamic environment, the fusion of virtualization and Command and Control (C2) servers emerges as a critical nexus, offering both enhanced control and strengthened security measures
6. The Future of Virtualization for Ethical Hackers and Red Teams: Look ahead to the future of virtualization technology and its potential impact on the evolving landscape of ethical hacking and red teaming. Discuss how virtualization will continue to evolve to meet the growing demands of the cybersecurity industry.

Web Developer | Cybersecurity Advocate | Offensive Security Enthusiast
Passionate about Personal Transformation and Offensive Security, I’m Ehinomhen Okaiwele—a dedicated Web Developer and Cybersecurity Advocate. My mission is clear: elevating the “Cybersecurity Consciousness” of fellow Africans. Through my journey, I aim to empower individuals, fostering a safer digital landscape for our community. Join me in this transformative endeavor.